|
|
Order by Related
- New Release
- Rate
Results in Title For hidden data like
 | After you took the Professor Von Patrick's gold, he captured six men from your team and he already killed one of them. Now you have to find the key to open the building where they are caught and save the other five. .. |
|
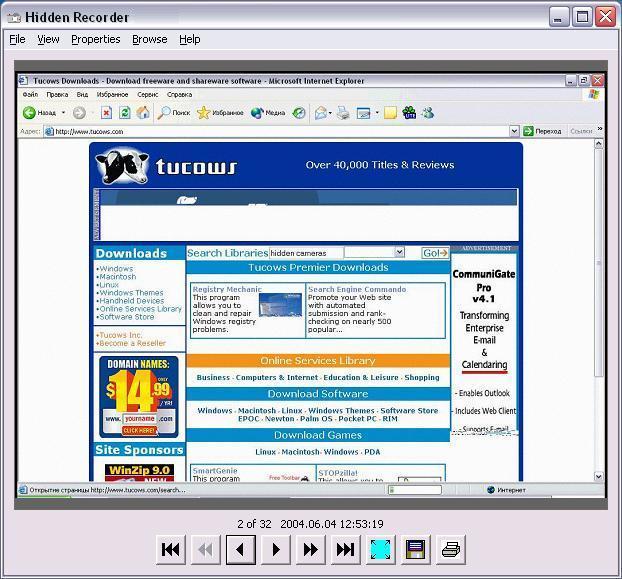 | Hidden Recorder is an invisible and easy-to-use PC activity monitoring tool that captures screenshots of the active application window or the entire desktop at the predefined time intervals varying from 5 seconds to 1 hour and saves the recorded images to a specified directory on the hard drive. The images can later be viewed with the built-in image viewer (press the Ctrl+F1 buttons simultaneously). This tiny and smart spy software can be used at home to control what the members of your family do on the PC when you are not watching. It is also a great employee monitoring and surveillance tool that can help you prevent the misuse of corporate resources and other, more serious, incidents. The program loads on Windows startup and quietly runs in the background completely hidden from everyone but you. It uses very little resources and does not degrade the performance of the system it is running on. The program can also be password-protected, so that even if someone learns the hot key, he or she will not be able to disable the snooper or modify any of its settings.
Main features
- Smart capture: the program does not make screenshots while screensaver or low power mode are running, also, it does not save the same screenshots
- Many settings
- Password protection
- Stealth mode
- Autostart mode ..
|
|
 | What you should know about ordering Elefun Wallpapers and Screensavers:
Payment information safety are ensured by RegNow - one of the most reliable systems of registration,
ordering and payment over the Web. RegNow is a company with a world-wide reputation.
It processes transactions in all basic currencies (USD, Pound Sterling, Euro) and supports various
forms of payment (all major types of credit cards, bank transfer, check, invoice, GIRO settlements).
30 Days money back guarantee. We guarantee that within 30 days since the purchase the money
will be returned to clients dissatisfied with our product.
After purchasing Animated Screensaver "Hidden River", you'll get :
*download link to full version of product.
*No Nag Screens in full version
*Unlimited Usage
*Technical support .. |
|
 | Priceless antiques have been stolen and hidden throughout Europe. The Professor calls upon her star student Adrianna to help her retrieve the stolen antiques. You will help Adrianna evade the evil thief as she travels Europe in search of the antiques. Mr. Gadget is also there to assist you. Solve his puzzles and he will give you cool gadgets like x-ray goggles, a diamond detector and more! It's a race to stop a thief, along with some seek and find fun, with Hidden Relics! ..
|
|
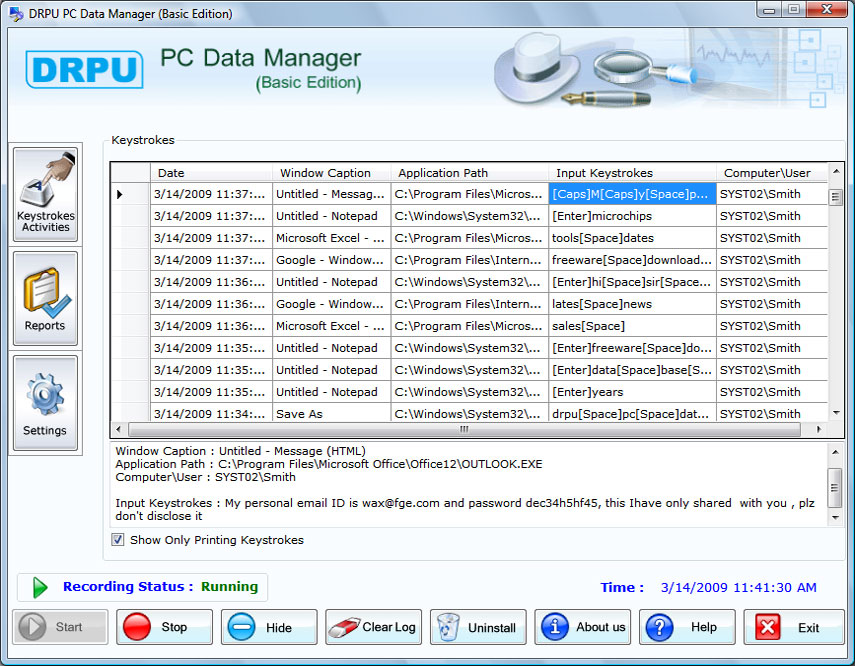 | Keyboard monitoring utility records each or every key pressed on keyboard with system timing details. Hidden keylogger software display data including sent/receive emails, online conversations, website URLs visited, passwords and document lists. .. |
|
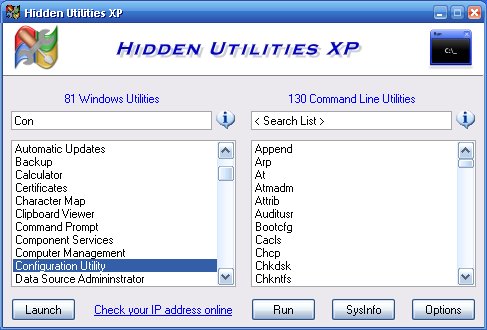 | Hidden Utilities provides easy access to over 200 utilities that are not easily accessible to the user. System information, diagnostics, repair tools and more in both Windows and Command Line utilities are now easily opened as well as many often ..
|
|
 | At the heart of Pure Hidden is a beautiful plant with buds that grow into flowers and, finally, reveal their ???fruit???, small boxes of moisturizer (66 in all). .. |
|
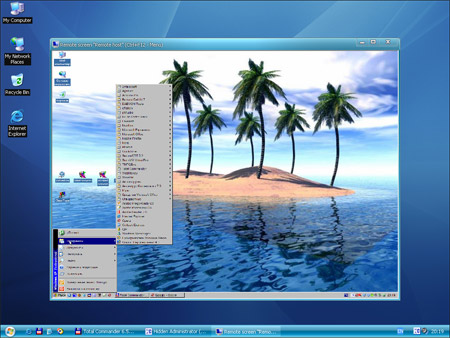 | The software is designed to administrate remote computers via a local network or the Internet. The program is easy to learn and use. It has a convenient and intuitive interface so even an unskilled user will be able to learn how to use it. .. |
|
 | Is your PC spying on you? Will your Internet history expose your privacy? Did you know that all your surfing history is being recorded in secret hidden files on your PC? Every website, files, movies, clips, documents, and anything else you viewed on your PC is recorded in secret hidden files on your hard drive. Did you also know that unwanted images, banners, pictures and content that exist on websites you visit, could be downloaded on your PC without your knowledge? Neteraser will delete hidden files and delete Internet history files and protect your privacy, family, job, business, and anything else you want to keep private - clear computer history and junk files with Net Eraser, the ultimate privacy tool. NetEraser is a privacy protector and system optimizer software tool that allows to completely clear all your online and offline activities, delete hidden files files, delete hidden files for browser search history, delete hidden files in address bar, delete hidden files in internet cache, delete hidden files in search engine, delete hidden files in search bar, delete hidden files in google, delete hidden files in yahoo, delete hidden files in msn, clear porn and objectionable files much more. .. |
|
 | Immerse yourself in a challenging expedition as you search for hidden objects and explore the historic Titanic! .. |
|
Results in Keywords For hidden data like
 | DB3NF is a Rapid Web Application Development platform (RAD) designed for fast and easy creation of high performance, maintainable and scalable Web applications of virtually any kind. It also dramatically reduces development and QA time and provides a consistent look and feel throughout the application.
DB3NF consists of six main parts ordered as they appear in the development process:
DB3NF Administration console. It allows creating and maintaining application schema and business rules. It also provides application administration and deployment.
"Schema" database. Schema database structure is fixed and the data is manipulated by the Administration Console. It defines and stores application structure, business rules and basic presentation rules. This database contains a set of deployment stored procedures. They read data from the Schema database and automatically create in the target ("Data") database a third normal form table structure with all necessary tables, primary, check and foreign key constraints, indexes and stored procedures.
"Data" database. This database is created automatically and its structure depends on the application schema.
Stored procedures are created automatically by the "Schema" database procedures. No development work is required to create and modify them when application schema changes. DB3NF component "talks" to the "Data" database exclusively through these optimized stored procedures, which provides for high performance of the DB3NF platform.
DB3NF component. The component is completely generic and integrates seamlessly with both databases. No design work is required after application schema is created and deployed. DB3NF automatically "learns" application schema and rules when application starts. The component employs various caching techniques and is extremely fast and efficient.
The ASP code in DB3NF is very simple and straightforward. It is easy to write and maintain... |
|
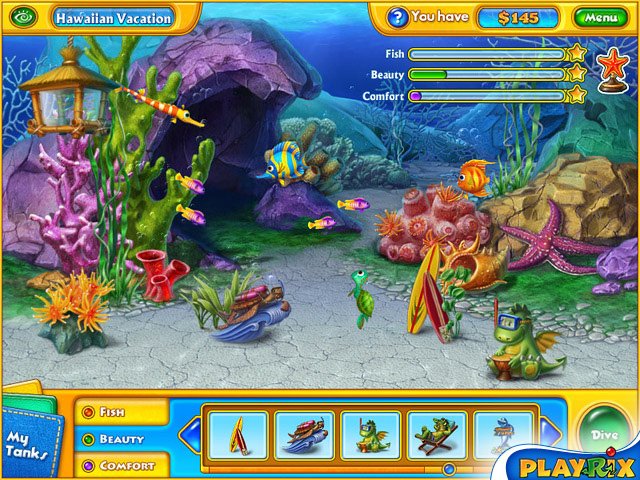 | Dive to the bottom of the sea and find various hidden items in numerous eye-teasing locations. Earn cash to buy cute sea creatures and beautiful ornaments and create three unique aquariums of your dreams!..
|
|
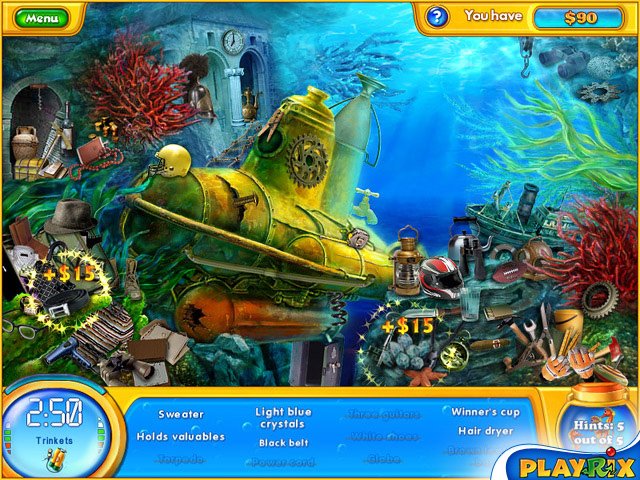 | Dive to the bottom of the sea and find various hidden items in numerous eye-teasing locations. Earn cash to buy cute sea creatures and beautiful ornaments and create three unique aquariums of your dreams in this Playrix game!.. |
|
 | At the heart of Pure Hidden is a beautiful plant with buds that grow into flowers and, finally, reveal their ???fruit???, small boxes of moisturizer (66 in all)...
|
|
 | After using your Ancestor?s Mirror to explore Castle Fairwich, you are sent back in time on a brand new quest! Your grandmother?s grandmother, Emma Willow, has built a time machine that has sent an entire train into the past!.. |
|
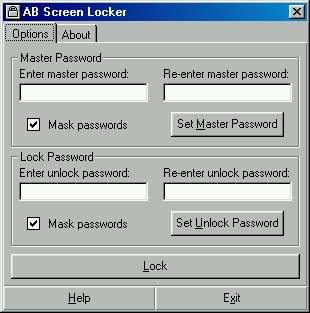 | A small utility that allows you to lock your screen. Any key combinations (like CTRL+ALT+DEL, ALT+TAB or CTRL+ESC) are disabled. If the system is restarted, this software will automatically load with Windows and your PC will be locked...
|
|
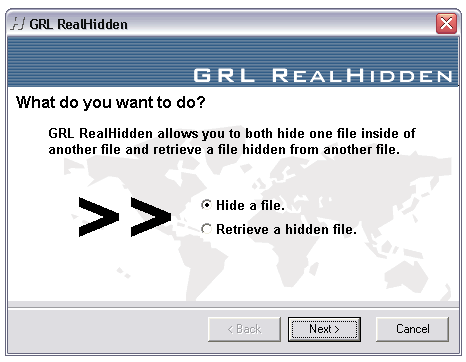 | GRL RealHidden version 1.0 is a software utility that allows you to hide a file physically inside of another file, and then retrieve that hidden file. The resulting 'cloaked' file, that is the file containing hidden file, usually operates exactly like the original file. This product gives you the power to send and receive files that contain hidden information, and the security of knowing that even if the files are intercepted a third-party probably would not know that they contained hidden information. In order to keep the final file size a low as possible, GRL RealHidden gives you the option of compressing the hidden file... |
|
 | Hidden Swap Buttons is a logic game. The purpose of the game is to gain as many points as possible. Points are added at the removal of the buttons. The buttons are removed at making a vertical or horizontal combination of three or more buttons of the same color. In order to create a combination like that you must switch two nearby buttons of different color in one round. Besides, if you are in urgent need of doing something else, instead of closing the game you can just hide it behind the limits of the screen. (The game is displayed neither in the tray nor in the taskbar). Then in your free time you can restore the game by mouse-moving at the edge of the screen and press the Ctrl key and continue playing. This game will come in handy not only at home, but also at the office where you will be able to play in your spare time, and, if necessary, hide it from the eyes of the others... |
|
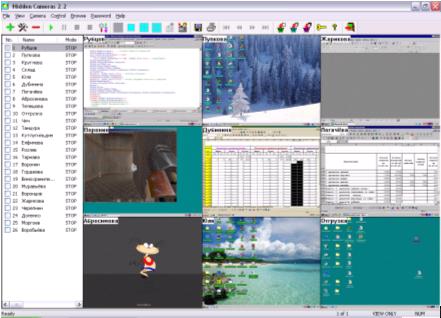 | Software Hidden Cameras Lite is intended for observation over computers in a local network with simultaneous with or without tracking. You can observe 5 computers at a time in the real time mode (you watch the monitor of one computer, the rest are tracked and can be watched later). The product makes screenshots of the PC monitors and saves them with intervals of 1 to 3600 seconds into an archive that may checked any time you wish... |
|
 | RePaintIt! provides the whole new way to play a Hidden Picture type of puzzle games. The aim of the game is to identify correctly a pattern hidden within the playing field image, which contains a number of black contours filled with different colors. Player is able to get Clue on general shape of the hidden pattern and/or Hints on the solution. Optional Game Modes could be used to make puzzle more challenging... |
|
Results in Description For hidden data like
 | Steganography enables you to use digital data hiding techniques (steganography) to hide and encrypt files within other files (carriers) such as picture or sound files. This allows you to encrypt sensitive information, while at the same time hiding it in a file that will not look suspicious, so nobody even knows that there is any encrypted information. The carrier files are fully functional and identical to the original files (except for size) , so if data was hidden in a picture file, the picture can still be viewed normally. The program gives you the option to hide a small text message, or one or more files that you select. It uses 256bit encryption, advanced compression and you can specify a password to extract the hidden files... |
|
 | RePaintIt! provides the whole new way to play a Hidden Picture type of puzzle games. The aim of the game is to identify correctly a pattern hidden within the playing field image, which contains a number of black contours filled with different colors. Player is able to get Clue on general shape of the hidden pattern and/or Hints on the solution. Optional Game Modes could be used to make puzzle more challenging...
|
|
 | AppHider used for hiding applications from another's eyes. The hidden windows are not visible in the Task Bar. In the hidden programs it is impossible to be switched by keys Alt+Tab !.. |
|
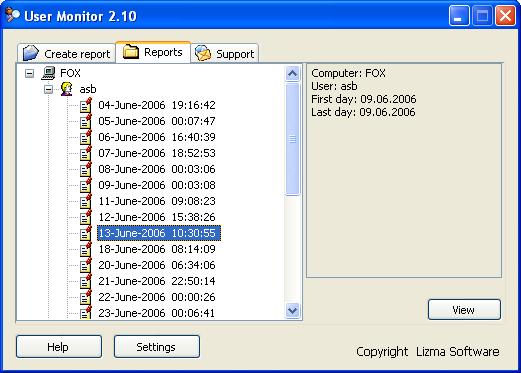 | The User Monitor is a program that performs hidden monitoring of a user's actions. The User Monitor controls all of the user's actions that were performed on the computer, it also provides information about the time spent on the computer, about the programs that were used and about the time spent on the current program.
The Hidden monitoring and data acquisition is performed during the user's session at the computer which has the User Monitor installed. Then, comprehensible logs are created using the data about all of the user's actions.
With the help of the User Monitor you can control and perform hidden monitoring of your employees' actions, and you can learn how much time they spend on ICQ or Web surfing and also more importantly on the work itself. You will know when the task was started and when it was finished, you will also have the information about the total time of the employee's absence.
You will also have the possibility to secretly control how much time your children spend playing games while you're not at home.
You will receive e-mail reports based on the acquired data about all the users' actions and will have the possibility to read them anytime and anywhere you want. You can also receive reliable information about the user's account without e-mail, in the offline mode. The User Monitor has a flexible interface and that allows you to configure reports about the users' actions to satisfy your requirements. The created reports are stored in a database and you can always read one of the previous reports.
The User Monitor supports SOS, which allows you to control and to perform hidden monitoring of all the users' activity on all of your server stations...
|
|
 | Estard Data Miner is a comprehensive data mining application, able to discover hidden relations both in structured and unstructured data. The newest data mining techniques were incorporated into this data mining software for carrying out automated data analysis. The program is a powerful end-to-end analytical solution. This data mining software can be used in business sector including: insurance industry, banking, finances (for example, determining and improving troubled business processes), marketing campaigns (costs decreasing and responce improving). A special feature of the program is that the discovered knowledge can be easily used for prediction. Besides, Estard Data Miner can be used in medicine, scientifical researches and even in military sphere. Some of the software functions are: importing data from various databases, statistical analysis, decision trees creation and revealing all rules which describe hidden correlations in data. Rules can be edited or deleted by users in case if they want to combine their own knowledge with discovered one. A special feature of the software is that created rules and decision trees can be easily used for quick analysis of any other databases, so you can save your time and resources. The automatization of data mining process doesnt demand special efforts from user. Thanks to built in wizards and user-friendly interface the user needs minimum time to start working with Estard Data Miner... |
|
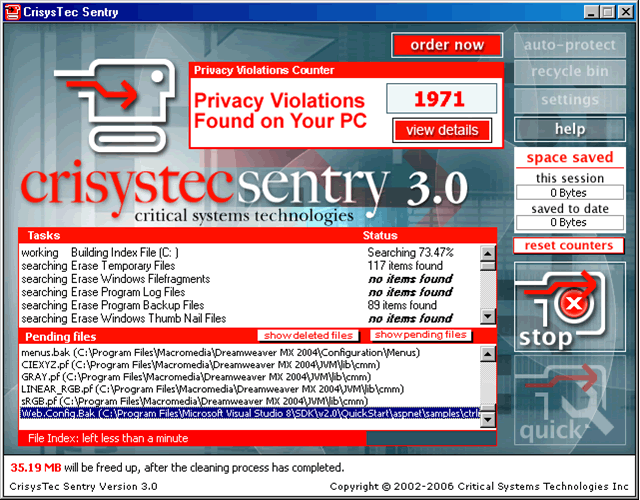 | Crisystec Sentry is an easy to use powerful and flexible data cleaning system for a single user Windows PC. Daily use protects you from unwanted data becoming permanently hidden in your PC. CrisystecSentry takes care of all of your privacy concerns...
|
|
 | Bedroom Hidden TV Cabinet - Make a change in your crib with the entertaining power of a bedroom hidden tv cabinet. Before choosing, learn the information available with this small and easy to use ebook type software. Bedroom hidden tv cabinet information... |
|
 | Reveal hidden Windows on your system - You may be surprised to learn how many programs run with no visible window. Sometimes, even keyboard monitor (spy) programs! This simple program will not reveal all hidden programs but if the program has a hidden window it will show it. It can be used - along with the Windows (R) Task Manager - as a diagnostic tool when trouble-shooting software installations. Try it. It is simple in form and function but may be invaluable when you need it. .. |
|
 | Cloak 7.0 is a powerful steganography application used to encrypt and hide confidential files within ordinary images. Files hidden with Cloak are not only undetectable, but cannot be retrieved without the correct passwords. Cloak uses advanced technology to protect and hide confidential information including: 256-bit encryption algorithms, 7 supported image formats, custom security certificates, advanced compression, and password protection of files. You can secure any file type with Cloak including '.exe' files. Images containing hidden files are fully functional and are identical to the original image. Cloak is an ideal tool for individuals who share very sensitive data with colleagues, family, or friends, and require that data to remain secure. Cloak is more than just an encryption application; it is also an electronic camouflage for your files. Other products just encrypt your files, but Cloak takes it a step further by hiding your files, thus making your data undetectable... |
|
 | ResourceExtract is a powerful tool that can extract all resource data from application file (.EXE, .DLL, .OCX, etc.). It can scan all file in selected folders or directory and find those hidden data in resource section. It can specify resource type to scan. It can specify file name to save. It very fast in extract resource data and easy to .. |
|
Results in Tags For hidden data like
 | Keyboard monitoring utility records each or every key pressed on keyboard with system timing details. Hidden keylogger software display data including sent/receive emails, online conversations, website URLs visited, passwords and document lists... |
|
 | Is your PC spying on you? Will your Internet history expose your privacy? Did you know that all your surfing history is being recorded in secret hidden files on your PC? Every website, files, movies, clips, documents, and anything else you viewed on your PC is recorded in secret hidden files on your hard drive. Did you also know that unwanted images, banners, pictures and content that exist on websites you visit, could be downloaded on your PC without your knowledge? Neteraser will delete hidden files and delete Internet history files and protect your privacy, family, job, business, and anything else you want to keep private - clear computer history and junk files with Net Eraser, the ultimate privacy tool. NetEraser is a privacy protector and system optimizer software tool that allows to completely clear all your online and offline activities, delete hidden files files, delete hidden files for browser search history, delete hidden files in address bar, delete hidden files in internet cache, delete hidden files in search engine, delete hidden files in search bar, delete hidden files in google, delete hidden files in yahoo, delete hidden files in msn, clear porn and objectionable files much more...
|
|
 | Hidden Recorder is an invisible and easy-to-use PC activity monitoring tool that captures screenshots of the active application window or the entire desktop at the predefined time intervals varying from 5 seconds to 1 hour and saves the recorded images to a specified directory on the hard drive. The images can later be viewed with the built-in image viewer (press the Ctrl+F1 buttons simultaneously). This tiny and smart spy software can be used at home to control what the members of your family do on the PC when you are not watching. It is also a great employee monitoring and surveillance tool that can help you prevent the misuse of corporate resources and other, more serious, incidents. The program loads on Windows startup and quietly runs in the background completely hidden from everyone but you. It uses very little resources and does not degrade the performance of the system it is running on. The program can also be password-protected, so that even if someone learns the hot key, he or she will not be able to disable the snooper or modify any of its settings.
Main features
- Smart capture: the program does not make screenshots while screensaver or low power mode are running, also, it does not save the same screenshots
- Many settings
- Password protection
- Stealth mode
- Autostart mode.. |
|
 | Hidden Swap Buttons is a logic game. The purpose of the game is to gain as many points as possible. Points are added at the removal of the buttons. The buttons are removed at making a vertical or horizontal combination of three or more buttons of the same color. In order to create a combination like that you must switch two nearby buttons of different color in one round. Besides, if you are in urgent need of doing something else, instead of closing the game you can just hide it behind the limits of the screen. (The game is displayed neither in the tray nor in the taskbar). Then in your free time you can restore the game by mouse-moving at the edge of the screen and press the Ctrl key and continue playing. This game will come in handy not only at home, but also at the office where you will be able to play in your spare time, and, if necessary, hide it from the eyes of the others...
|
|
 | This tool can read/extract the values from protected storages in Windows. If you lost your password to some online resource, you may recover this information from saved cache.. |
|
 | Message Smuggler software | smuggle or hide text message into image | 256-bit encryption algorithm and password protect. Create secret picture message with certified 256-bit encryption algorithm and password protection. - absolute security..
|
|
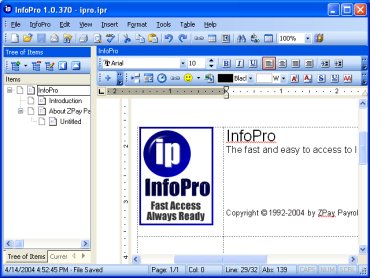 | InfoPro manages your bits and pieces of information without having to manage multiple files. It can handle anything from a to-do list to complex notes. You can collect all your bits and pieces of information into a "hierarchical collection of notes"... |
|
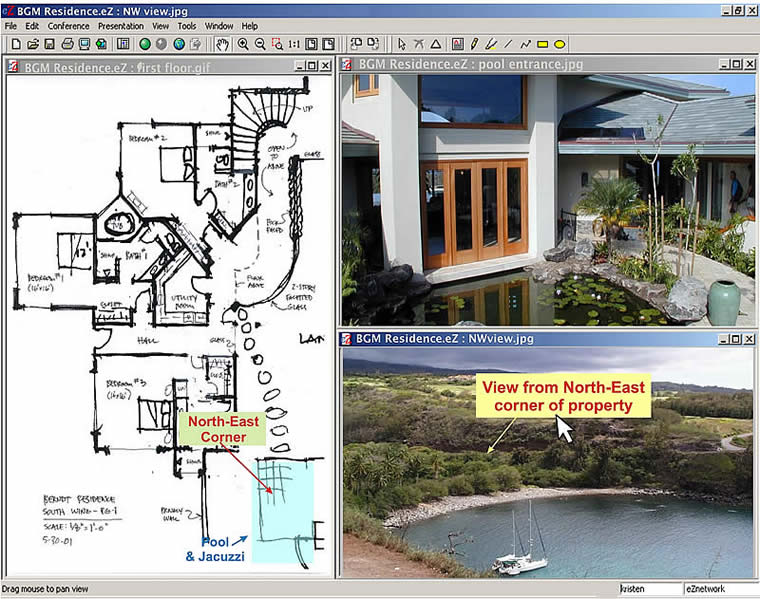 | Simple, free universal viewer for PDF, CAD, 3D Models, Word, Excel, PowerPoint, digital photos: JPG, GIF, BMP, and more. Open multiple files of different type at once and tile to see them all on your screen at once. View compound .ez presentations... |
|
 | NetSearch is a powerful utility designed to search local area networks (LAN) for all kinds of files. In contrast to standard Microsoft Windows.. |
|
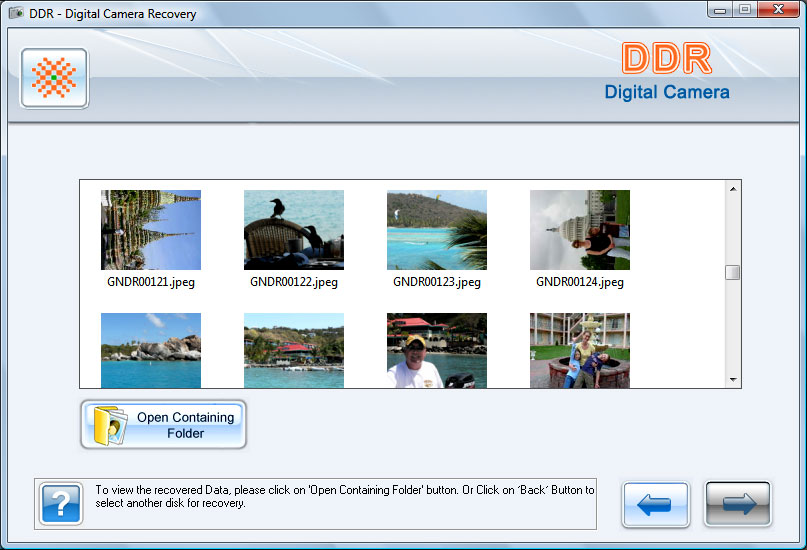 | Innovative recover camera images utility uses most advanced and cutting edge data recovery algorithms to scan formatted, corrupted or logically damaged digital camera storage media to locate and restore missing picture, audio and video files... |
|
Related search : idden filesdelete hidden,delete hidden filesbar delete hiddenfiles delete hiddensecret hidden fileshidden recorder,recorder hidden recorderhidden recorder hiddenswap buttonshidden swap,hidden swap buttonsbuttons hidden swapswap buttons hidden,messageOrder by Related
- New Release
- Rate
hidden file -
hidden treasure -
hidden webcam -
hidden menu -
hidden camera 2.1 -
|
|


























